Introduction
Microsoft Sentinel has a great MITRE ATT&CK page that shows you which tactics and techniques are being covered by your rules. It looks like the image below (this is from a new MS Sentinel instance, so I don’t have any rules enabled)
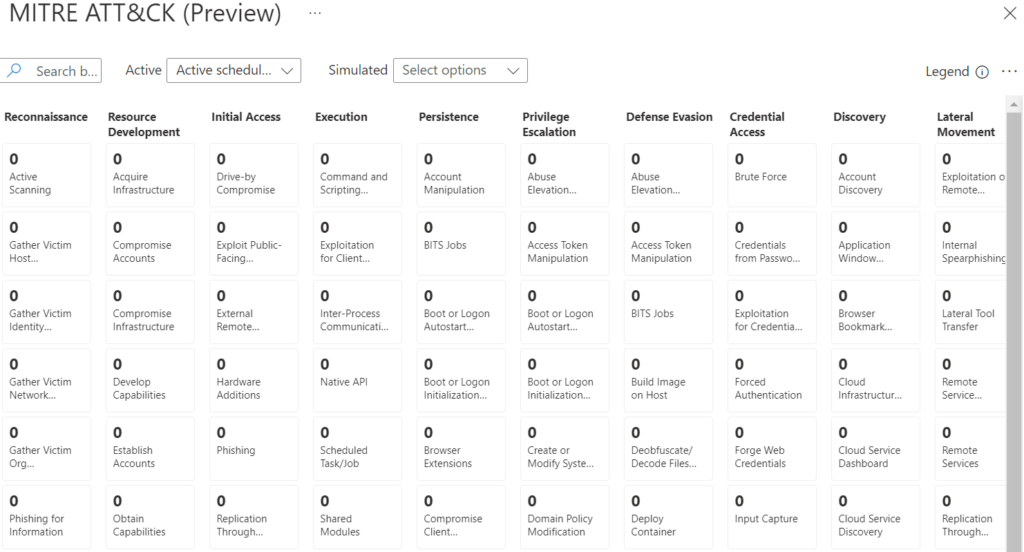
It would be great to get this information into a CSV file so it can be manipulated further. This blog post will show you how to do that.
Just a reminder that before you run this PowerShell script, make sure you are logged into your Azure tenant and are in the correct subscription to get the correct information. Go to garybushey/ExtractMITRE: Extract MITRE ATT&CK information (github.com) to get the file.
Getting the MITRE names
This means getting the actual names and descriptions of the MITRE tactics and techniques and wasn’t too hard to do thanks to the Programmer’s Tools in the Microsoft Edge Browser (see my blog How do I determine what API Microsoft Sentinel is using? – Yet Another Security Blog (garybushey.com) if you are not familiar with the tool). I was able to load the page, and then search for some of the titles to find how the page loads the names. It turns out there is a JavaScript file that gets loaded which contains all the needed text. Some copy, pasting, search & replace and they were converted into hashtables and available to use in a PowerShell script.
Getting the counts
This was actually pretty easy, once I figured out how to store the data so that it can be converted into a CSV file easily. I ended up using a datatable. It allows for custom columns and to easily add new information. I thought about using a dictionary, but it will not allow duplicate keys and I could not decide on a good key to use that was distinct.
To create the object, I use the following code
$outputObject = New-Object system.Data.DataTable
[void]$outputObject.Columns.Add('Tactic', [string]::empty.GetType() )
[void]$outputObject.Columns.Add('Technique', [string]::empty.GetType() )
[void]$outputObject.Columns.Add('Name', [string]::empty.GetType() )
[void]$outputObject.Columns.Add('Count', [string]::empty.GetType() )
[void]$outputObject.Columns.Add('Description', [string]::empty.GetType() )This creates the new object with the needed columns. The columns are
- Tactic – The name of the tactic
- Technique – The technique’s ID number (i.e T1595)
- Name – The technique’s name (i.e. Active Scanning)
- Count – How many rules use this tactic and technique combination (remember, that different tactics can use the same technique)
- Description – The technique’s description
Once I load the active rules using the Microsoft Sentinel REST API to load the alert rules, I then iterate through the tactics. In each tactic, I then iterate through its techniques.
I have included a parameter to either include or ignore those alert rules that are disabled. It is up to you if you want disabled rules to be counted or not. The Microsoft Sentinel MITRE ATT&CK page does NOT count them, which makes sense since disabled rules are not providing coverage. By default, my script will not count them either.
Next, I count how many rules use the tactic and technique combination (and, if needed, if the rule is active). That gets saved as a new row as shown below
foreach ($tactic in $tacticHash.keys) {
foreach ($technique in $tacticHash[$tactic]) {
$count = 0
if ($IncludeDisabled) {
$count = ($results.properties | Where-Object { ($_.techniques -eq $technique) -and ($_.tactics -eq $tactic) }).count
}
else {
$count = ($results.properties | Where-Object { ($_.techniques -eq $technique) -and ($_.tactics -eq $tactic) -and ($_.enabled -eq $true) }).count
}
$newRow = $outputObject.NewRow()
$newRow.Tactic = $tactic
$newRow.Technique = $technique
$newRow.Name = $techniqueNameHash[$technique]
$newRow.Count=$count
$newRow.Description = $techniqueDescriptionHash[$technique]
[void]$outputObject.Rows.Add( $newRow )
}
}Once this is complete, it is just a simple matter of writing the object to a CSV file. If you have looked at any of my earlier PowerShell scripts I wrote for Microsoft Sentinel, you will see I am using a new way of doing this. This new way is much more efficient and I will probably go back and rewrite the old code to use this new way.
$outputObject | Export-Csv -QuoteFields "Description" -Path $filenameThat is all there is to it. Of course, I am not showing the 550+ lines of code that make up the tactic and technique information, but you can look at the code to see that.
You cannot quite duplicate the layout of the Microsoft Sentinel screen in Excel (or at least I couldn’t) but you can use a pivot table to get a nice report as shown below:
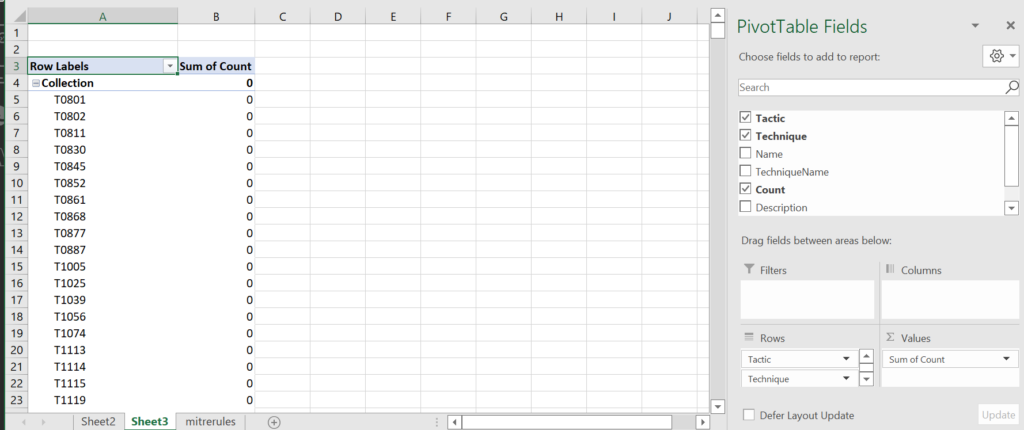
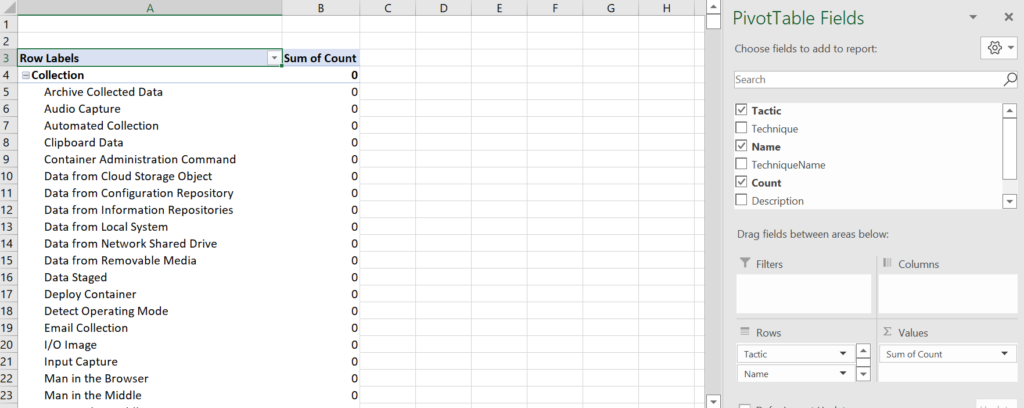
This gives some good information, if you happen to have memorized the technique number. You can replace “Technique” in the rows with “Name” like I did below
One other thing you can do, is to create a new column that combines the technique’s number and name into a single field and use that. If you notice, in the list of the fields, I have done that and called it “TechniqueName”. I used that in the pivot table shown below
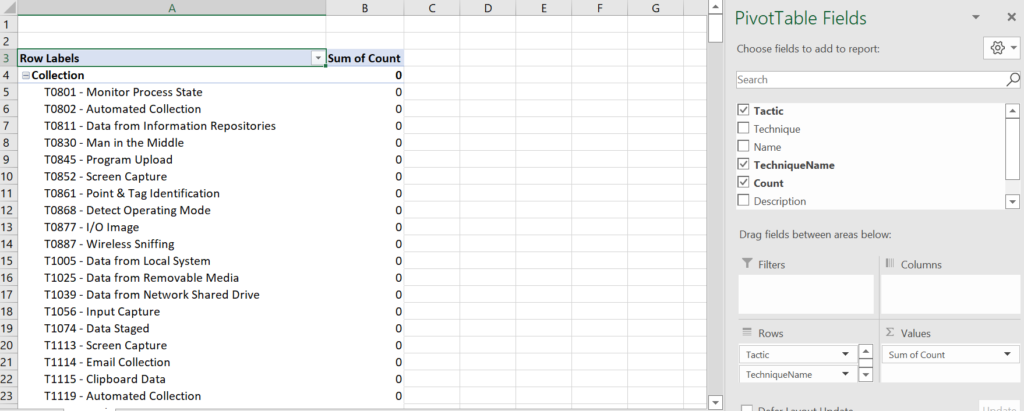
If you are going to setup your pivot like shown in Figure 4 above, I would suggest modifying the code to create the field for you automatically. It isn’t hard.
Summary
This blog post walked you through how to extract the MITRE ATT&CK information that is shown in Microsoft Sentinel into a CSV file. From there, you can do all sorts of manipulations or reports as needed.
One thought on “Extract Microsoft Sentinel MITRE information to CSV file”
-
Pingback: Extract Microsoft Sentinel MITRE information to CSV file – Part II – Yet Another Security Blog
Leave a Reply