Microsoft quietly released the Incident settings page in the Scheduled Analytics rule wizard. On this page you can state whether you want the alert to create an incident, if the alerts should be grouped into a single alert, and if you want to re-open closed incidents when a new alert is generated.
The page looks like the image shown below and again, it is only, currently, available when creating/editing a Schedule rule.
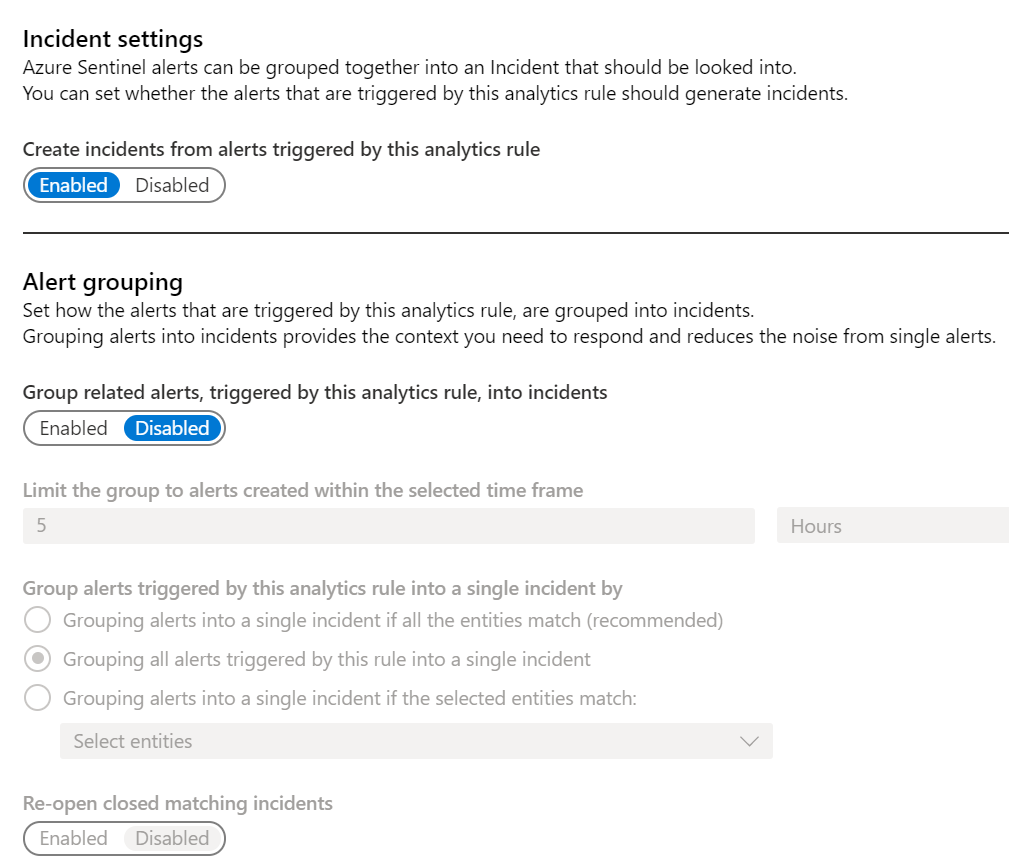
Most of the fields should be self-explanatory but the options under Group alerts triggered by this analytics rule into a single incident by field could use a little more explanation.
- Grouping alerts into a single incident if all the entities match (recommended) – Select this field if you want the alerts to combine into a single Incident if and only if ALL the entities that are part of this alert match. As the field’s title states this is the recommended selection and is the one that would cause the fewest incidents of unrelated alerts being combined into one incident, although it could still happen.
- Grouping all alerts triggered by this rule into a single incident – This will group all the alerts into one incident no matter what the entities’ values. While this is usually safe and a lot of times what you want, keep in mind if you are alerting on something like a mass file download, it is probably better to have an incident for each alert so that they may be investigated separately.
- Grouping alerts into a single incident if the selected entities match – This is almost like the first option except that instead of matching on all the entities, you get to choose one or more entities to match on. This will be useful if you have something like an alert that tracks access to servers. You would probably want to match on the IP and Host, as these are the values that determine the server, but the Account could be different if different people are logging in. By selecting the IP and Host to match on, you can ensure that all the activities for each server are in a single incident.
As you can see, this is going to be a powerful addition to Analytics rule. Keep in mind the first sentence under the Alert Grouping header: “Set how the alerts that are triggered by this analytics rule, are grouped into incidents. ” What this means is that only alerts from the same rule can be grouped together.